コレクション opsec process is a decision-making step 685835-What is the five step opsec process
Answer Which step in the OPSEC process is a decisionmaking step because it helps the decision maker prioritize and decide whether or not to assign a countermeasure? · OPSEC is a fivestep iterative process that assists an organization identifying specific pieces of information requiring protection and employing measures to protect them 1Which step in the OPSEC process is a decisionmaking step because it helps the decision maker prioritize and decide whether or not to assign a countermeasure?
2
What is the five step opsec process
What is the five step opsec process-The first step towards a decisionmaking procedure is to define the problem Obviously, there would be no need to make a decision without having a problem So, the first thing one has to do is to state the underlying problem that has to be solved You have to clearly state the outcome that you desire after you have made the decisionThey either Answer this question Operations Security (OPSEC) Annual Refresher January 23, 21 / in



Cyber Operational Planning Springerlink
· When decision making, there are many steps that can be taken;EPub Opsec Awareness Training Answers OPSEC is an analytical process that safeguard's information about our operational intentions and capabilities The process succeeds by Step 1 OPSEC Process In this step, you determine what information is available to the adversary that could be used to harm your mission and its effectiveness · Which step in the OPSEC process is a decision making step because it helps the decision maker prioritize and decide whether or not to apply a countermeasure?
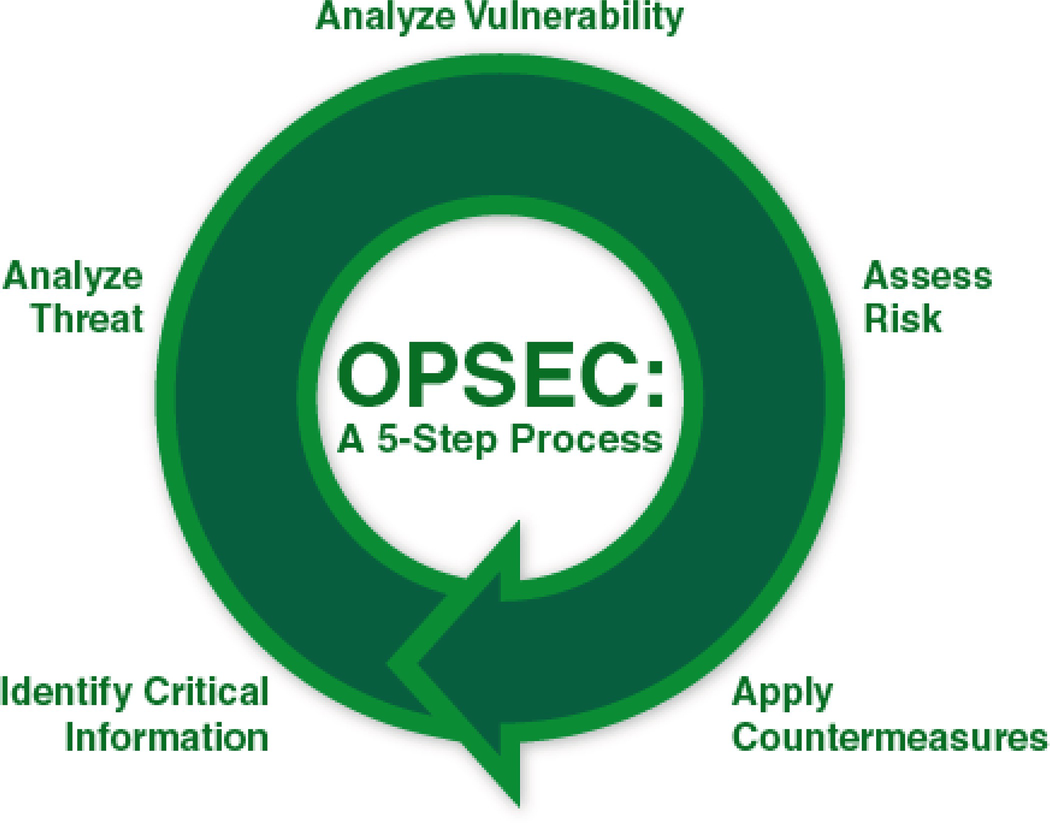
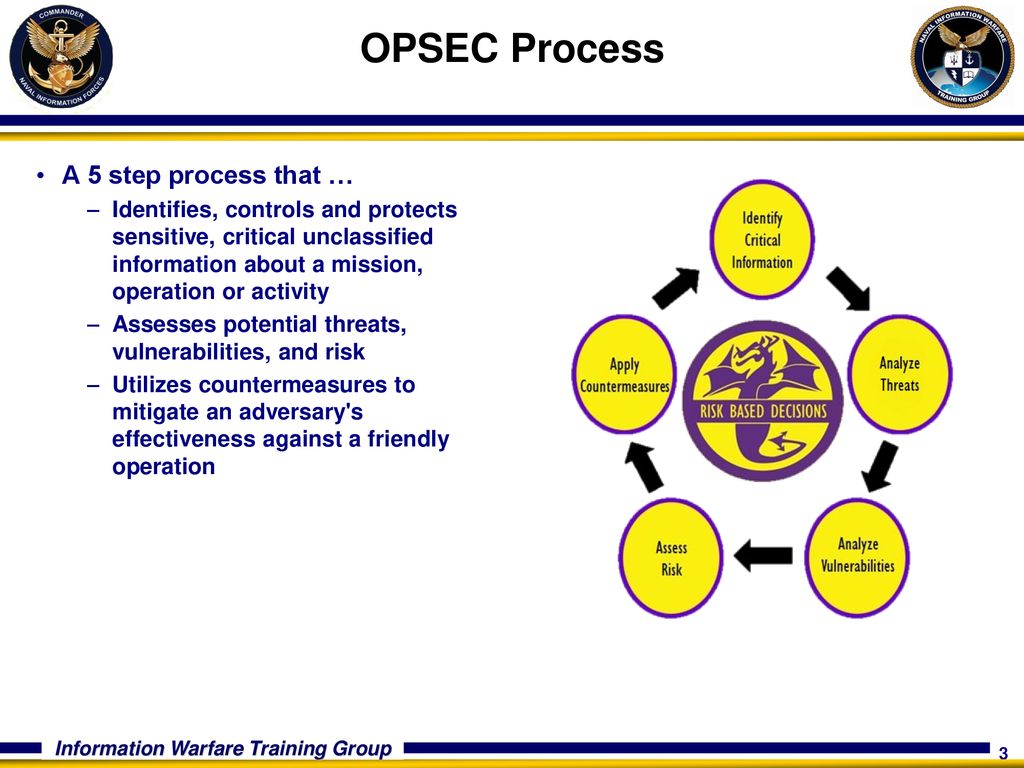
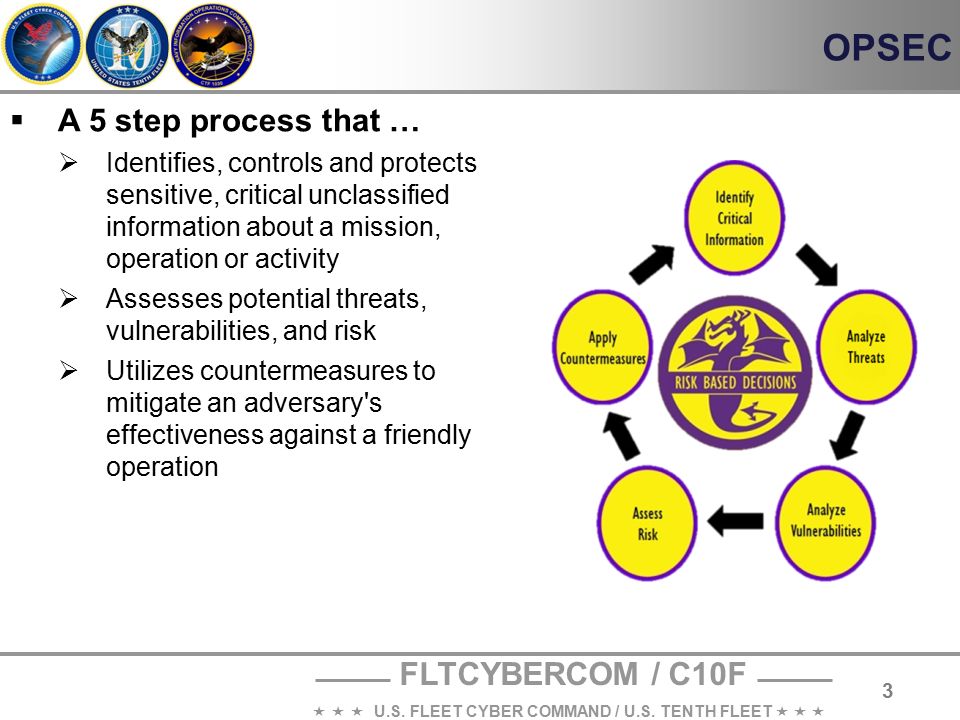
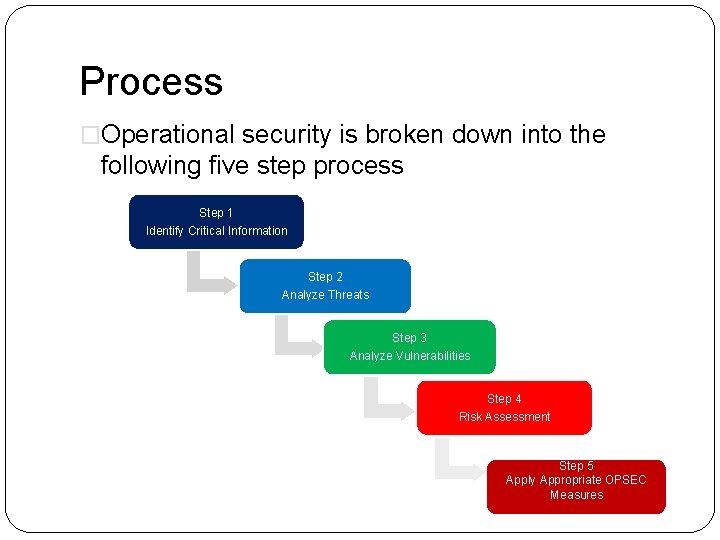
Basis for effective adversary decision making 2 Identify Critical Information a The identification of critical information is a key part of the OPSEC process because it focuses the remainder of the OPSEC process on protecting vital information "Little minds try to defend everything at once, but sensible people look at the mainBut when making good decisions there are really only five steps that need to be considered These steps are as follows Step 1 Identify Your Goal One of the most effective decision making strategies is to keep an eye on your goalThe OPSEC process involves five steps (1) identification of critical information, (2) analysis of threats, (3) analysis of vulnerabilities, (4)assessment of risk, and (5) application of appropriate countermeasures Your paper should be Three (3) pages in length, and all sources used should be cited and referenced using APA formatting
· The step is assess risk Which step in the OPSEC process is a decision making step because it helps the decision maker prioritize and decide whether or not to apply a countermeasure?In a more general sense, OPSEC is the process of protecting individual pieces of data that could be grouped together to give the bigger picture (called aggregation) OPSEC is the protection of critical information deemed missionessential from military commanders, senior leaders, management or other decisionmaking bodiesThe 5 Step OPSEC Process Step 4 Assess the Risk •Decisionmaking process balances vulnerabilities against threat determines if risk warrants applying corrective actions (countermeasures) •Decisionmaker either accepts the risk or implements countermeasures •Decisionmaker weighs cost of recommended




Paul Davis On Crime Analyze This Opsec Is Key In The War On Terrorism



2
The identification of critical information is a key part of the OPSEC process because It focuses the remainder of the OPSEC process on protecting vital information rather than attempting to protect all unclassified information It is the fifth and final step of the OPSEC processRisk assessment is a decisionmaking step because it helps the decision maker prioritize and decide whether or not to assign a countermeasure to a vulnerability · OPSEC analysis provides decisionmakers with a means of weighing how much risk they are willing to accept in specific operational circumstances in the same way as Operational Risk Management (ORM) allows Commanders to assess risk in mission planning In fact, OPSEC can be referred to as information risk management



2



2
This document identifies and describes five key elements needed to perform a comprehensive analysis of threat the identification of an adversary, the development of generic threat profiles, the identification of generic attack paths, the discovery of adversary intent, and the identification of mitigation · Step #4 Evaluate each option After collecting data, we can use it to measure the pros and cons for each of the potential solutions / responses Once we measure the pros and cons, we can rank the options It can be difficult to rank options when the basis of ranking is not obvious · Commonly shortened into "OPSEC," it is a fundamentalif not the most importantpart of military operations OPSEC refers to all the different ways




Comsc Instruction 3070



2
IO is the integrated employment of three operational elements influence operations (IFO), electronic warfare operations and network warfare operations IO was narrowed to these five core capabilities for three reasons * They are operational in a direct and immediate sense;A risk assessment is a decisionmaking step to determine if a countermeasure needs to be assigned to a vulnerability based on the level of risk this vulnerability poses Step 5 – Apply OPSEC Countermeasures Let's review Step 5 of the fivestep process Step 5 Apply OPSEC CountermeasuresThe determination of risk is a demanding step in the OPSEC Process It requires a degree of subjective decision making based on the best estimate of an adversary's intentions and capabilities Included in the assessment of an adversary's capability is not only his ability to collect the information but also his capability to process and exploit (evaluate, analyze, interpret) in time to



2



2
Image 1 OPSEC Cycle 9Federal Communications Commission (US) explains the steps of OPSEC model in business and IT context, although the essential principles and steps are the same for all sectors An OPSEC process should follow 5 steps A Identifying critical information B Analyzing threatsC Analysis of vulnerabilities D Risk assessment EAssess risk correct Risk is a function of the 126 People Learned More Courses ›› View Course · 7 Steps for an Effective DecisionMaking Process Having a plan is the first step, but then there are seven after that, so consider this the set up Without a plan or a process in place, you'll never be able to develop a method of decisionmaking that holds true



2



2
FM 34 31 Chapter 3 MILITARY DECISIONMAKING PROCESS (MDMP) MDMP in General FM 1015 is the doctrinal source The MDMP is a single, established, and · The OPSEC process involves five steps (1) identification of critical information, (2) analysis of threats, (3) analysis of vulnerabilities, (4) assessment of risk, and (5) application of appropriate countermeasures Just so, what is the primary goal of opsec?OPSEC is the protection of critical information deemed mission essential from military commanders, senior leaders, management or other decisionmaking bodies The process results in the development of countermeasures, which include technical and nontechnical measures such as the use of email encryption software, taking precautions against




Operations Security Opsec Ncms Antelope Valley Chapter




Distribution Headquarters Employees Participate In Opsec Jeopardy Defense Logistics Agency News Article View
/10/18 · Researchers have studied the managerial decisionmaking process and have identified six stages that go into making an informed decision The initial step is simply to understand that a choice must be made because the status quo no longer holds or something external has forced a change in the organizationIt is on the fifth training day Stock level 1 Army Opsec Level 1 Ttp This document describes the rationale for NICS, the principal components that make it function, A risk assessment is a decisionmaking step to determine if a countermeasure needs to be assigned to a vulnerability based on the level of risk this vulnerability poses · Which step in the opsec process is a decision?



2



2
· What is the process?The steps for developing our own OPSEC are Step 1 Make a list of any critical information you have that can be used by an adversary Step 2 Determine who your adversaries are Step 3 Look at all the ways your critical information can be compromised StepAnswer Assess risk Most relevant text from all around the web




Operations Security Wikipedia




Mdmp How To Guide
The 5 Steps of OPSEC The OPSEC 5Step Process provides a holistic picture, a systematic process for mission success and an analytical methodology for assessing critical information 1) Identify Critical Information 2) Analyze Threats 3) Analyze Vulnerabilities 4) Assess Risk 5) Apply CountermeasuresThe determination of risk is a demanding step in the OPSEC Process It requires a degree of subjective decision making based on the best estimate of an adversary's intentions and capabilities Included in the assessment of an adversary's capability is not only his ability to collect the information but also his capability to process andWhich step in the OPSEC process is a decisionmaking step because it helps the decision maker prioritize and decide whether or not to assign a countermeasure?




Making Data Driven Decisions In Rapidly Changing Conditions Supply And Demand Chain Executive




Eidws 111 Opsec
Incorporated into operations and planning, identifies each step of the process, suggests several items to consider for operations security guidance, and provides an example of an operations security estimate Chapter 3 examines an operations security planner's role in each step of the military decisionmaking processWhich step in the OPSEC process is a decisionmaking step because it helps the decision maker prioritize and decide whether or not to assign a countermeasure?What are the elements of threat?



Operations Security Opsec Pdf Free Download



2
· In general, the decision making process helps managers and other business professionals solve problems by examining alternative choices and deciding on the best route to take Using a stepbystep approach is an efficient way to make thoughtful, informed decisions that have a positive impact on your organization's short and longterm goalsThe decision making process involves the following steps Curious Observation Existence of Problem Goals & Planning Search, Explore & Gather the Evidence Generate Creative & Logical Alternative Solutions Evaluate the Evidence Make theA is incorrect The correct answer is D The level of risk to the organization determines whether a countermeasure will be assigned to the vulnerability



2



2
· OPSEC is the protection of critical information deemed missionessential from military commanders, senior leaders, management or other decisionmaking bodies The process results in the development of countermeasures, which include technical and nontechnical measures such as the use of email encryption software, taking precautions againstOPSEC Project Proposal Summary This could be either by reduction or elimination of the exploitation OPSEC project will comprise of several steps that are vital in examining, planning, preparing executing and sustenance of the state of operations after the execution phase people who are charged with the decision making process will beA is incorrect The correct answer is D The level of risk to the organization determines whether a countermeasure will be assigned to the vulnerability




Operational Security Best Practices Fasrnerd



2
Which step in the OPSEC process is a decisionmaking step because it helps the decision maker prioritize and decide whether or not to assign a countermeasure?Answer Identify critical information Apply countermeasures Assess · Risk assessment is a decisionmaking step because you decide if a countermeasure needs to be assigned to a vulnerability based on the level of risk this vulnerability poses to your mission, operation, or activity OPSEC Fundamentals Course – TEXT ONLY VERSION




Operations Security Wikipedia




Information Operations The Actions Taken To Affect Adversary
OPSEC is an operations function, not a security functionTrue or False OPSEC is a process to deny potential adversaries information about capabilities and/or intentions by identifying and controlling generally unclassified evidence of the planning and execution of sensitive activities2 OPSEC Process The OPSEC process is a five step process Those responsible for OPSEC program creation/implementation shall apply this fivestep process that entails a Step 1 Identification of Critical Information The commander and staff tries to identify the questions that




The Mitre Att Ck Framework Where Do You Start




Page United States Army Field Manual 3 13 Information Operations Djvu 65 Wikisource The Free Online Library



2



2



2



2



2



Step By Step Instructions For How To Purchase Business Software In



2



2



2



2



Operations Security Opsec Pdf Free Download




Strategic Decision Making Applying The Analytic Hierarchy Process N Bhushan K Rai 1 By Victor E Cardozo Delgado Issuu



Cyber Operational Planning Springerlink




Annex Z4 Opsec Eefi



2




Xorl Eax Eax Page 6




Pin On Military Planning




Operations Security 16 August August Ppt Download



Forensiq Inc Security And Counterintelligence Awareness




Xorl Eax Eax Page 6




Overall Classification Of This Briefing Is Unclassified Fouo Ppt Video Online Download



2




Opsec Security




Cyber Operational Planning Springerlink



2



Command Indoctrination Operations Security Dd Mmm Yy Ppt Download



2




Operations Security Opsec Program Pdf Free Download



2




Doc Applying Opsec To Terrorism Fred Milker Academia Edu




Information Operations The Actions Taken To Affect Adversary




Joint Doctrine For Operations Security Iws The Information




Joint Publication Operations Security Pdf Free Download



2




Opsec Process Summary Glossary Course Map Mute Voice Transcript Opsec Process Circle Identify Critical Information Analyze Threat Analyze Vulnerabilities Assess Risk Apply Countermeasures Critical Information Is Information An Adversary Needs To



2



2



2



2



Protect Your Opsec



2



2



2




Describe Operational Security Opsec Bst Docx Describe Operational Security Opsec Training Support Package Tsp Battle Skills Test Bst 17 Task Course Hero




Operations Security Opsec U S Navy



2



Overall Classification Of This Briefing Is Unclassified Fouo Ppt Video Online Download



2




Ppt Information Operations Powerpoint Presentation Free Download Id



2




Ppt Good Security Is A Group Effort Powerpoint Presentation Free Download Id




Opsec For Preppers Should I Be Paranoid North Country Survival




Information Operations The Actions Taken To Affect Adversary




Eidws 111 Opsec



2



2




Fm 34 100 4 Chapter 2




Chesbro On Security Operations Security Opsec



2




Operations Security 16 August August Ppt Download



Operational Security Learning Topics Introduction Critical Information Threat




Mco 3070 2 The Marine Corps Operations Security Opsec Program



Section 2 Intelligence Collection Activities And Disciplines Operations Security Intelligence Threat Handbook




Xorl Eax Eax Page 6




Operations Security Opsec Ppt Download




Book Review Of Practical Cyber Intelligence By Wilson Bautista Jr Security Boulevard




Joint Publication Operations Security Pdf Free Download




Intent And Capability In Order To Analyze The Threat You Need To Identify All Course Hero



2



2



Layer 8 Linux Security Opsec For Linux Common Users Developers And Systems Administrators Lg 164




Intent And Capability In Order To Analyze The Threat You Need To Identify All Course Hero



1


コメント
コメントを投稿